Not known Factual Statements About Ip Camera
Ip Camera Fundamentals Explained
Table of ContentsWhat Does Ip Camera Do?Not known Details About Ip Camera The Best Guide To Ip CameraSome Known Details About Ip Camera Ip Camera - The FactsFascination About Ip Camera
The video can be made use of as a method of determining as well as capturing transgressors. (P2P) network., therefore providing the surveillance counterproductive. Axis Communications. Fetched 11 July 2017.
A Biased View of Ip Camera
29 September 2016. Recovered 14 July 2017. "Quick as well as Faster". Computer Publication. 3 December 1996. p. 9. Gotten 14 July 2017. (PDF). Axis Communications. Fetched 18 November 2017. "An Incredibly Unboring History of IP Cameras". Protect America. 12 September 2016. Obtained 11 July 2017. Daily, Financier's Organization (2021-09-30). "Just how Ring's Owner Developed A Buzzer Well Worth $1 Billion To Amazon.com".
IFSEC Global. 2016 - ip camera."Web Procedure (IP) Cameras - Just How do They Job & What are the Benefits?

7 Easy Facts About Ip Camera Shown
Fetched 2020-02-12. Recovered 2022-06-17."Monitoring Video camera Market is anticipated to get to US$ 45.
Fetched 2022-06-17. Blackstone, Sara (October 27, 2019). "Home Surveillance Cameras - Regional vs. Cloud Video Storage". Protect Thoughts. Obtained November 9, 2019. Cornett, Ben. "Introduction to Security Electronic Camera Technologies". EZWatch. com. Gotten 22 August 2014. Alexandr Lytkin. IP Video Clip Security. A Crucial Overview, 2012, 978-5-600-00033-9. "House Protection". Wireless IP Cameras.
"Leading 4 Advantages of Relocating from analog to IP video surveliance". frontier-security. com. Recovered 2 October 2018. Cassel, David (July 23, 2019). "Are We All Set for AI-Powered Safety And Security Cameras?". The Information stack. Fetched November 9, 2019. Wollerton, Megan (October 31, 2019). "The most effective face recognition electronic cameras of 2019". CNET. Obtained November 9, 2019.
Some Known Factual Statements About Ip Camera
CNET. 14 September 2017. Retrieved 2 October 2018.
Recovered 19 February 2017. Network Globe.
As with most tech services, however, house protection video clip setups are targeted by cyberpunks and also crawlers. Protect yourself by following some common feeling security-hardening treatments. A lot of modern other IP safety cams feature user-upgradeable firmware.
Generally, you can upgrade your video camera's firmware from the admin console through a web browser. You must frequently check your IP safety and security electronic camera manufacturer's website for updated firmware to ensure that you can make certain the variation you utilize does not have an unpatched susceptability that can be manipulated by cyberpunks as well as online voyeurs.
The Facts About Ip Camera Uncovered
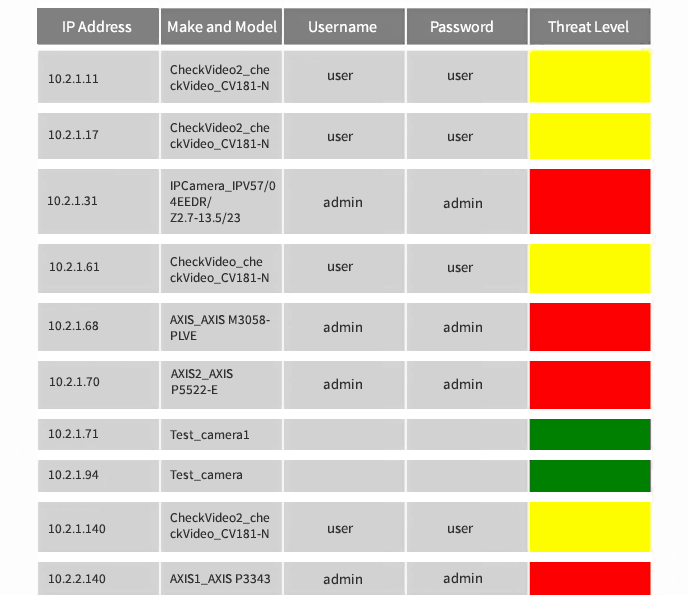
Lots of IP cameras don't have password security transformed on by default. Some individuals neglect to include password defense after the initial setup and end up leaving the cams open for all to accessibility.
Your electronic camera's default admin name and password, set by the manufacturer, is typically offered by visiting their site as well as going to the support area for your cam model. If you haven't altered the admin name and also password, the most amateur cyberpunk can look up the default password as well as watch your feeds or take control of your electronic camera.
Do not place an IP safety and security video camera inside locations of your house where you wouldn't feel comfy being seen by unfamiliar people. Also if you assume you protected your video cameras in every way feasible, there is constantly the possibility of getting additional hints blind-sided go to these guys by a Zero-Day susceptability that hasn't been located by your maker.